Cyber attacks by various groups with different motives frequently target Armenia. These motives can be broadly categorized as either criminal or political/geopolitical. For this discussion, we will focus on the latter.
As expected, Azerbaijan frequently launches cyber-attacks against Armenia. However, the hackers involved in these attacks belong to diverse groups. Some are known as patriotic groups, while others are part of various state structures or under their control. Furthermore, Azerbaijan also hires mercenaries, mostly independent hacker groups operating in the CIS, to carry out specific tasks for money. Additionally, Azerbaijan actively purchases spy software from the market, mainly Pegasus.
At present, neither Azerbaijan nor Armenia are among the influential states that have professional and long-term hacker groups capable of carrying out extensive and sophisticated attacks.
From the perspective of attacks carried out by state-sponsored hacking groups, the most active against Armenia and Armenian targets—although it may appear surprising to some—is the Russian APT 28 team.
Who are APT 28?
Fancy Bear, also known as APT28, is a well-known Russian hacking group affiliated with the GRU, the Russian military intelligence agency. It has been operating since the mid-2000s and mainly supports Russian political interests. The group targets government, military, and security organizations in the South Caucasus, post-Soviet states, and NATO allies.
They have carried out cyber attacks against various high-profile institutions, including the German and Norwegian parliaments, TV5Monde, NATO, the White House, the Democratic National Committee, and participants in Hillary Clinton’s and French presidential candidate Emmanuel Macron’s campaigns.
APT 28 goes by different names (depending on the cyber threat lab):
- Fancy Bear
- Pawn Storm
- Sofacy Group
- Sednit
- Forest Blizzard
- Tsar Team
- STRONTIUM
- ITG05
Fancy Bear in Armenia: recent cases
Recently, we learned about the latest attacks against Armenia.
In February 2024, a state-sponsored hacking group known as APT 28 launched multiple phishing attacks on organizations in several countries, including Argentina, Ukraine, Georgia, Belarus, Kazakhstan, Poland, Armenia, Azerbaijan, and the United States. These attacks were reported by IBM X-Force in March 2024.
In September 2023, ESET reported targeted attacks by APT 28 on government institutions in Ukraine, Armenia, and Tajikistan.
Fancy Bear in Armenia: targeting military and diplomatic entities
Ten years ago, APT28 initiated their first known attacks against Armenia. In a report published by FireEye (now known as Trellix) in October 2014, it was revealed that APT28 registered a domain and used it to target the Armenian military by installing a phony email login page.

The trick that APT 28 used was both simple and brilliant. The genuine domain of the RA Ministry of Defense is Mil.am, while the fake one is RNil.am. The only difference between the two domains is one pixel. APT 28 was able to install a fake Yahoo login page through this fake domain.
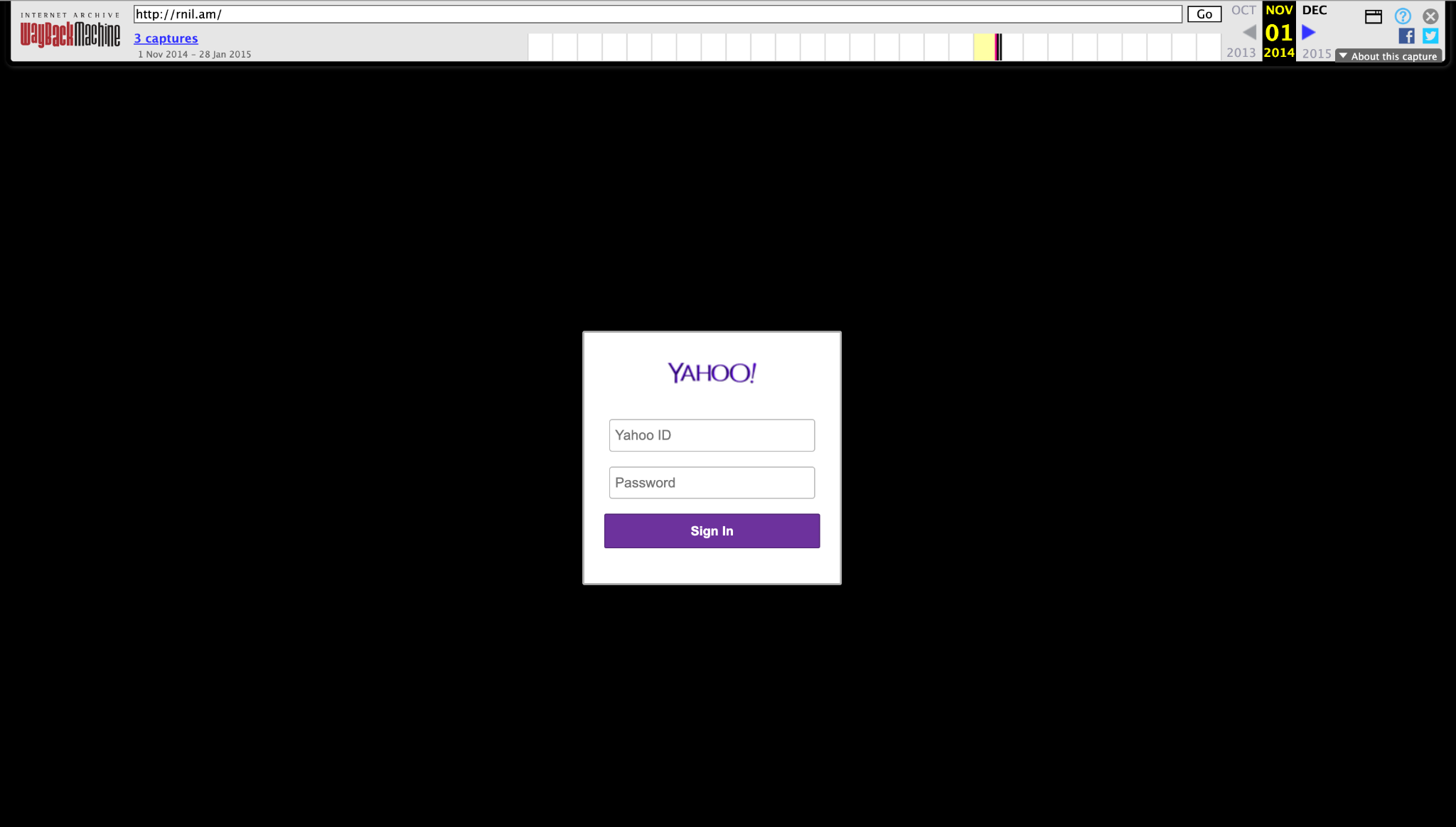
According to the report by Trend Micro, a fake domain, mail.rnil.am, was used as a tool in a phishing campaign targeting the Armenian military.
In 2015, APT 28 registered yet another counterfeit domain for phishing attacks. This time, the hackers aimed at Armenian diplomats using webmail-mfa.am.
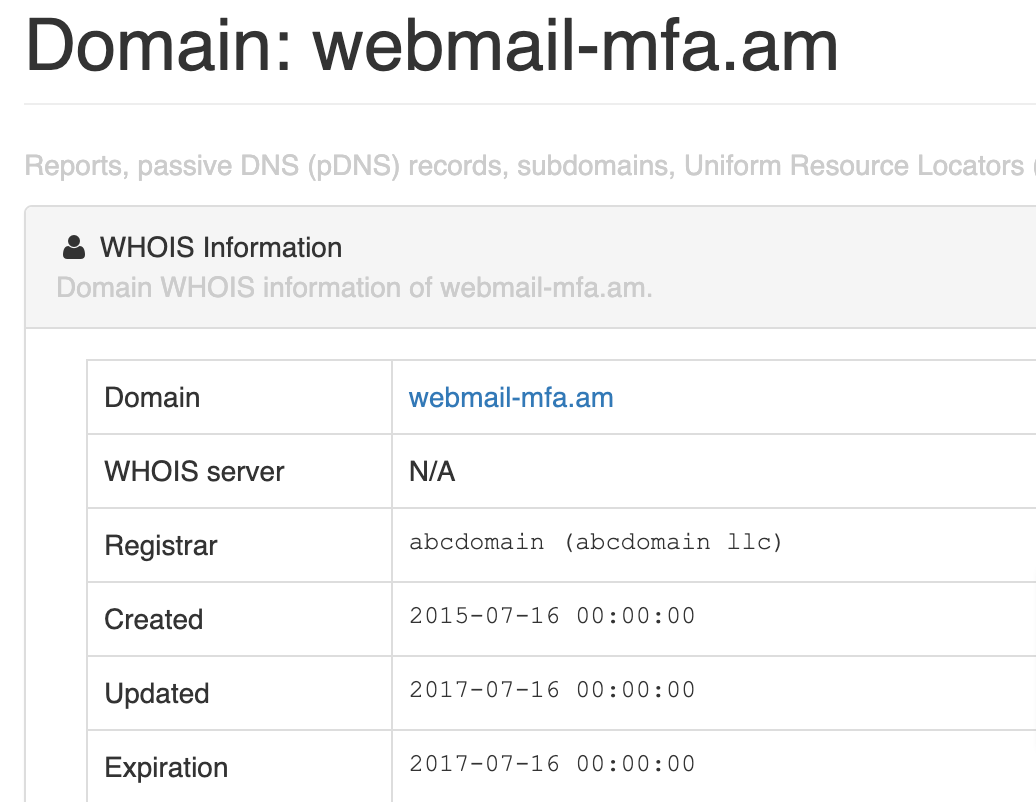
During the military attack against Artsakh by Azerbaijan in early April 2016, an individual created a fake domain that resembled the website of the Armenian Foreign Ministry. The domain included a mail server mail.rnfa.am. However, the domain was blocked immediately, and there is no concrete evidence to determine whether the perpetrators were APT 28 or the Azerbaijani intelligence used a similar method to imitate the Armenian Foreign Ministry’s website.
In 2017, Citizen Lab reported a mass phishing and disinformation hybrid attack that involved APT 28. This group is known for carrying out hybrid attacks, where cyber attacks are used as part of influence operations. The most well-known of these attacks were the large-scale attacks on the Democrats during the 2016 American elections.

This large-scale hybrid campaign also targeted Armenian politicians and military:
- Politicians, civil servants and government officials from Afghanistan, Armenia, Austria, Cambodia, Egypt, Georgia, Kazakhstan, Kyrgyzstan, Latvia, Peru, Russia, Slovakia, Slovenia, Sudan, Thailand, Turkey, Ukraine, Uzbekistan and Vietnam.
- Military personnel from Albania, Armenia, Azerbaijan, Georgia, Greece, Latvia, Montenegro, Mozambique, Pakistan, Saudi Arabia, Sweden, Turkey, Ukraine and the United States, as well as NATO officials.
Next steps: civil society is also a target
In 2017, a massive global phishing attack against journalists and activists was revealed. Once again, by Fancy Bear or APT 28. And again, Armenia was among the main targets.
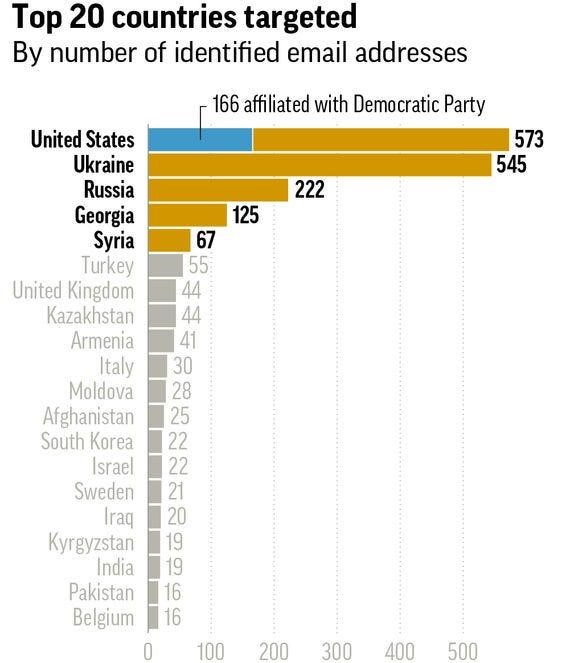
In Armenia, APT 28 targeted over 40 individuals, including journalists, members of civil society, and political analysts. On June 26, 2015, Fancy Bear targeted Maria Titizian, the editor of EVN Report. Titizian linked the attack to Electric Yerevan.
The following information lists some of the known attacks by APT 28 against Armenian targets, but it is likely that these are only a small portion of the group’s overall activity. APT 28, also known as Fancy Bear, employs highly sophisticated techniques, which means that many of their attacks can go unnoticed. However, it is clear that Armenia has been and will continue to be a primary target for this group.
It should be noted that various Russian state affiliated groups, including Turla associated with FSB and Ember Bear group attributed to GRU, were active in Armenia.







